What are the types of access control? In this article, we’ll provide an overview of the different types of access control systems and how they play a critical role in safeguarding your office.
Understanding Access Control: The Foundation of Security
 |
Access control is a critical component of any security strategy, ensuring that only authorized individuals gain entry to specific areas within an organization. By implementing robust access control systems, businesses can protect sensitive data, safeguard physical assets, and maintain a secure environment for employees and visitors.
Different types of access control systems meet an organization’s unique needs and security requirements. Understanding the foundation of access control is essential for building a comprehensive security strategy.
Role-Based Access Control: Simple Management for Static Permissions
Role-Based Access Control (RBAC) is a widely used method of managing employee access. By assigning specific roles to employees based on their job functions, RBAC ensures that individuals only have access to the resources necessary for their roles. This minimizes the risk of unauthorized access and helps maintain a secure work environment.
Administrators must define roles and permissions according to security requirements. RBAC is a more rigid but straightforward approach to enhance security.
Discretionary Access Control: Flexible Security for Dynamic Environments
 |
Discretionary Access Control (DAC) offers a more flexible approach to managing access permissions. This method is particularly useful in dynamic environments where individual access requirements change frequently.
With DAC, administrators can grant or revoke access permissions individually, providing a high level of control. However, this flexibility also requires careful management to prevent unauthorized access and ensure consistently enforced security policies.
Mandatory Access Control: High-Level Security for Strict Access Environments
Mandatory Access Control (MAC) is a highly secure method of managing access permissions, typically used in environments where the protection of sensitive information is paramount. Unlike DAC, where resource owners control access, MAC enforces strict access policies set by a central authority, ensuring that only authorized individuals can access specific resources.
Government, military, and other high-security environments where the potential consequences of unauthorized access are severe often use MAC. Although MAC lacks flexibility and simplicity, it allows organizations to consistently enforce access permissions.
Visitor Management Systems with Video Capabilities: Enhancing Security with Professional Services
 |
Visitors’ access requires a tool different from that of employees. Visitor management systems often include access control functionality, but providing a welcoming and professional visitor experience is essential to maintain client trust.
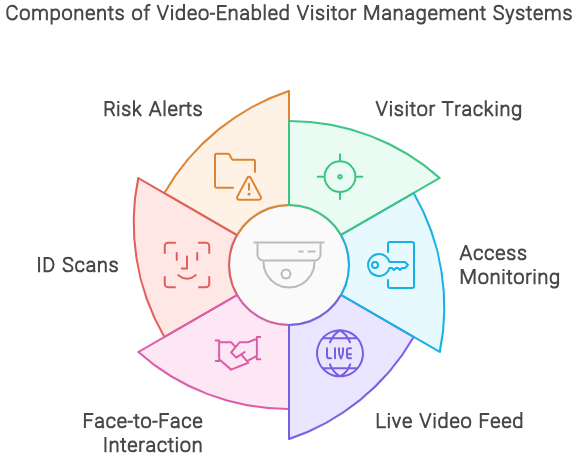
Visitor Management Systems that include video capabilities provide staff with live video of the visitor and lobby before allowing access. Two-way video calls also build trust with your client using remote face-to-face interaction with your staff. ID verification of visitors, screenings, and visitor activity notifications further inform your team of who is on-site and any known risks.
Visitor access control systems offer flexibility to adapt to visitor needs; however, maintaining a professional visitor experience is essential.
Making Informed Decisions on Integrated Access Control Systems
Integrating various access control systems tailored to your organization’s needs is crucial for a secure and efficient business environment. By combining employee and visitor-based access systems, businesses can enhance security and streamline access management. Ultimately, these tools foster a safer and more productive workplace for employees and visitors alike.

